Deepfake Roundup: How Deepfake Detection Tools Protect Against Digital Deception
As deepfake technology grows more sophisticated, businesses face an alarming rise in digital fraud and impersonation.
Home > Digital media authenticity > Page 4

As deepfake technology grows more sophisticated, businesses face an alarming rise in digital fraud and impersonation.

The Attestiv ROI Calculator helps insurance professionals quantify the real cost of AI-generated fraud — and how much you can save with Attestiv’s fraud detection platform.
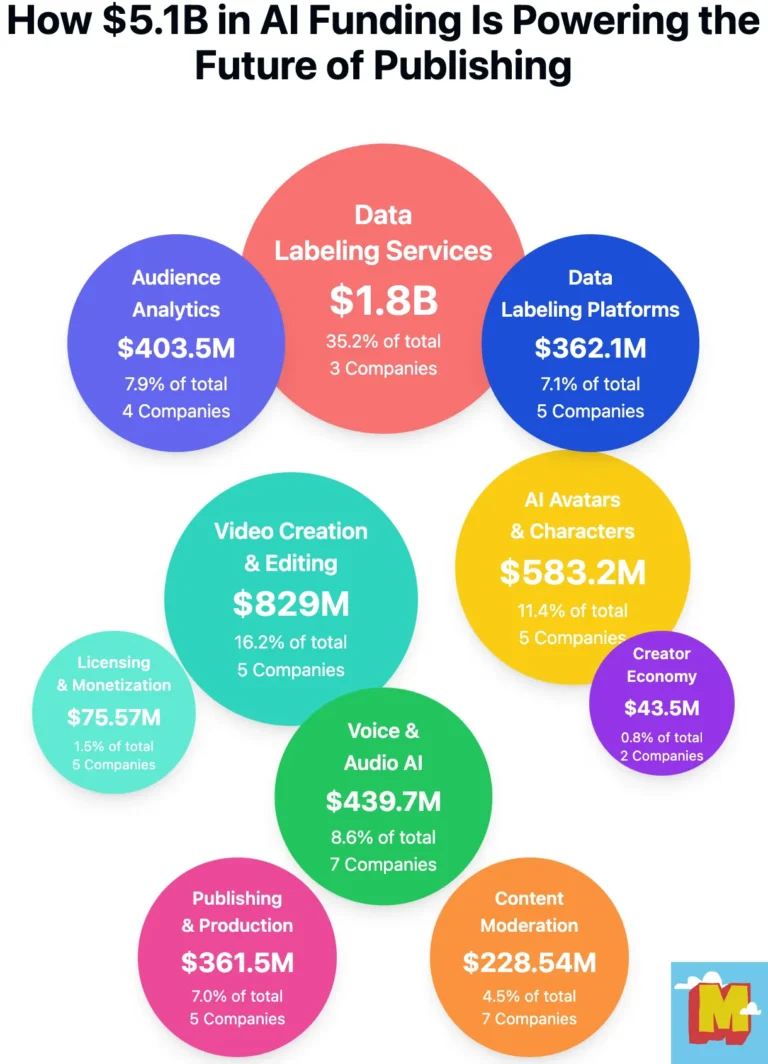
Attestiv ranked among the top companies in Content Moderation & Integrity

Attestiv now offers a comprehensive solution tailored for HR departments to stop deepfakes and fraudulent photos, videos and documents
Kenyan fact-checker Pesacheck uses Attestiv to help debunk deepfake earthquake video

Attestiv selected as #1 Cybersecurity company in Lehi by F6S.

Attestiv identified as a cutting-edge Countermeasure. With its sophisticated authentication platform, it has raised the bar against attackers, even as they push the envelope of deceptive realism.

Attestiv CEO Nicos Vekiarides weighs in on the threat.

The Tungsten Marketplace, a destination for custom-developed solutions to extend and enhance existing automation investment, has added Attestiv,
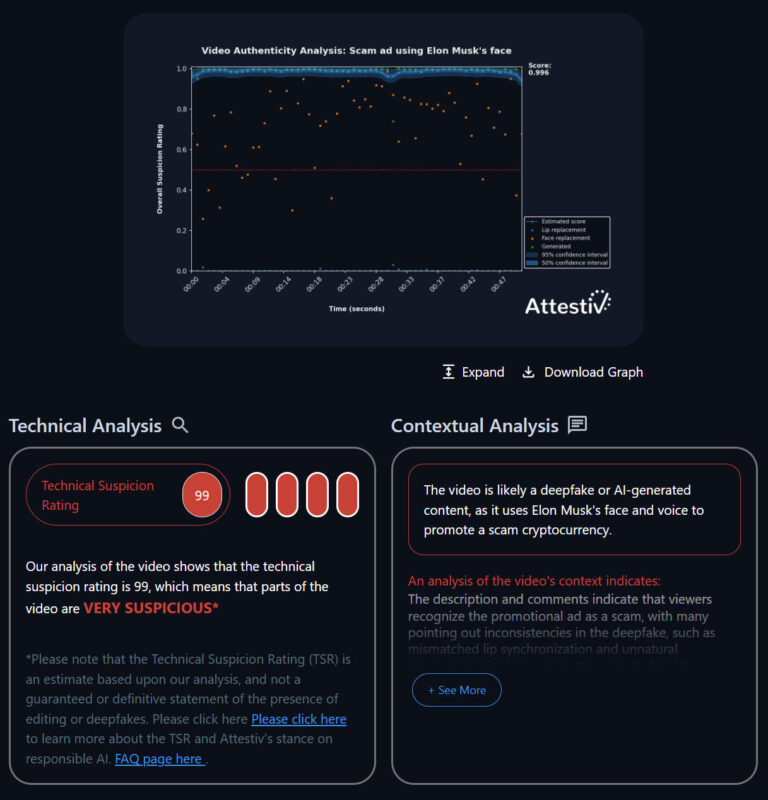
Advanced AI-powered video analysis to detect deepfakes is available to businesses and consumers starting at no cost

Mark Morley is the Chief Operating Officer of Attestiv.
He received his formative Data Integrity training at Deloitte. Served as the CFO of Iomega (NYSE), the international manufacturer of Zip storage devices, at the time, the second fastest-growing public company in the U.S.. He served as the CFO of Encore Computer (NASDAQ) as it grew from Revenue of $2 million to over $200 million. During “Desert Storm”, Mark was required to hold the highest U.S. and NATO clearances.
Mark authored a seminal article on Data Integrity online (Wall Street Journal Online). Additionally, he served as EVP, General Counsel and CFO at Digital Guardian, a high-growth cybersecurity company.
Earlier in his career, he worked at an independent insurance agency, Amica as a claims representative, and was the CEO of the captive insurance subsidiary of a NYSE company.
He obtained Bachelor (Economics) and Doctor of Law degrees from Boston College and is a graduate of Harvard Business School.